- You are here:
- Home »
- Blog »
- Manage Your Computer Business »
- BitLocker 101: Easy, Free Full Drive Encryption for Windows
BitLocker 101: Easy, Free Full Drive Encryption for Windows
If there’s something undeniable about the prevalence of mobile computing devices today, it’s that they are becoming increasingly vulnerable to loss and theft. The Ponemon Institute found in 2008 that 4800 laptops are lost every single day at USA airport checkpoints. In 2010, Intel released results from its ‘Billion Dollar Lost Laptop Study‘ which found that, among 329 businesses/organizations studied, a collective average of $6.4 million worth of laptops were lost each year.
There were some other interesting points from the Billion Dollar Lost Laptop study such as:
- Only 5% of lost laptops are ever recovered.
- 70% of lost laptops lack any form of security like encryption or anti-theft protections.
- There is a 7.12% chance that any laptop will be stolen during a 3.1 year lifespan.
- Education and research workers have the highest risk of laptop loss at 10.85%.
How many of these risks could be easily prevented? Most, if not all, of them as a matter of fact. Thanks to Windows BitLocker, which has been present in Windows since the release of Vista, seamless full drive encryption has been possible for quite a few years now.
While other options have been available as well, like the open-source TrueCrypt or Seagate’s FDE (Full Disk Encryption) line of laptop HDDs, all of these third party solutions add an extra layer of complexity that BitLocker avoids. Since BitLocker is baked right into Windows Vista, 7, and 8, there is not much more a user has to do besides enable the technology and they’re set. No special hardware, software, or user intervention needed.
I’ve personally come late to the game in using BitLocker, as I only turned the technology on when I switched my primary Thinkpad laptop to Windows 8 Pro last year. Call it ignorance or lack of self education, but I never took the chance to educate myself on how easy this technology was to employ and benefit from. Since I feel this Windows feature could greatly benefit both technicians and customers alike, I’m sharing my own knowledge on the technology in this article.
Why is BitLocker better than alternatives like TrueCrypt or Seagate FDE drives?
There are numerous reasons why using native Windows functionality is beneficial over third party solutions. In the case of TrueCrypt (a software I previously used years before with decent success) you are forced to install a program that requires additional configuration and another dependency that has to run in the background to negotiate the encryption/decryption process. While TrueCrypt is fairly transparent, the authors’ refusal to support TPM chips built into many laptops today is another benefit which BitLocker provides.
Seagate FDE drives are beneficial in that they remove the layer of software that TrueCrypt requires, but their innate downside, and a rather hefty one, is that you have to purchase these special HDDs in order to benefit from the technology. There are relatively few higher end business laptops which offer these out-of-the-box, and even then, the price point that these units come in at is usually higher than what could be achieved merely through a copy of Windows with BitLocker with the same benefits. Secondly, this technology is not offered on any SSD drive yet.
For the above reasons, I think Windows BitLocker provides the highest level of file encryption security with the perfect balance of cost and convenience.
How does BitLocker work?
BitLocker provides full volume encryption on any volumes (even Windows boot volumes) by working in conjunction with encryption keys that are automatically generated during the BitLocker initiation process. For systems that have TPM chips (like my Thinkpad T410) the encryption/decryption process is completely transparent and seamless. Windows works in conjunction with the TPM chip to check on numerous boot variables of the host system to ensure that there are no signs of tampering. If the chip signals the all clear to Windows, a normal boot ensues straight into your OS of choice.
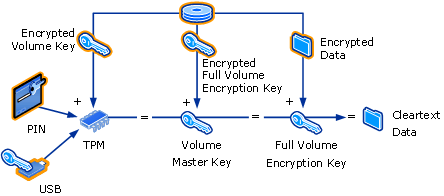
For systems that do not have TPM chips, like most desktops, the BitLocker boot process can be enabled via the use of a USB encryption key that is easily generated during the BitLocker initiation. If this USB key is inserted and present on your system, normal boot will be allowed and plays the same part as the TPM chip. However, systems with TPS chips are the easiest way to enable and utilize BitLocker because a USB key is much easier to lose than a chip planted on a motherboard. For added protection, users can enable the use of an extra PIN code that needs to be entered even if the USB key or TPM chip is present.
In short, BitLocker requires nothing more than a capable version of Windows and a computer with a TPM chip (preferred) or a BitLocker enabled USB key. A full in-depth guide on BitLocker operation can be found at Microsoft TechNet.
What versions of Windows include BitLocker?
Windows Vista and 7 both have BitLocker baked into the Ultimate and Enterprise editions. Windows 8 offers BitLocker in the Pro and Enterprise flavors as well (including on the Surface Pro tablet). The Surface RT tablet offers basic full disk encryption as long as the user signs into their device with a Microsoft account.
When Microsoft releases its free Windows 8.1 upgrade, it has been reported that all editions of Windows 8 will include the basics of BitLocker full drive encryption but without the management aspects offered in Windows 8 Pro and Enterprise. This means any system running Windows 8.1 should have some form of disk encryption capability later this year.
Can I use BitLocker on portable drives like USB thumb sticks?
The short answer is yes! If your copy of Windows (see above) supports native BitLocker functionality (7 and 8 only – no Vista, sorry) then you also have the capability to use BitLocker to Go. This extension of BitLocker provides full disk encryption for any range of portable devices from USB thumb drives to external hard drives.
The nice part about BitLocker to Go is that you can get read-only access to the files on such devices on any edition of Windows since XP with a simple add-on utility from Microsoft called BitLocker to Go Reader. You won’t be able to save files onto the drive, but this is a great way to reference items no matter what Windows flavor you may have access to.
Can I use BitLocker on Windows Server?
Microsoft has been including BitLocker support in every edition of Windows Server since the 2008 release. This is handy because you can now add an extra layer of security to the server closet with relative ease, using the same procedures that are outlined for protecting client OS systems like desktops and laptops. Even servers that employ RAID technology (hardware RAID; not cheap software RAID) can take advantage of BitLocker.
Is there hardware that runs better with BitLocker?
BitLocker in general is a fairly low-impact feature that can function on nearly any system available today. There is something to be said for systems that have later generation Intel Core i5 and i7 processors, since TomsHardware has reported that Intel has caked new AES extensions into newer processors which reduces some of the necessary computing overhead. This is only a nicety, and not a requirement, by any means.
Personally, I would much rather have a desktop or laptop with a TPM chip on the motherboard to take advantage of native transparent BitLocker operation without the need for a USB key. While there is no short list of systems that generally offer TPM chips, most business oriented computers tend to have them as standard fare. I like to recommend Lenovo’s Thinkpad and Thinkcentre computers to my FireLogic customers, for example, and all models I have worked with offer these chips by default.
What if someone tries to access my drive via a live CD or connected to another system? Does BitLocker still keep my data safe?
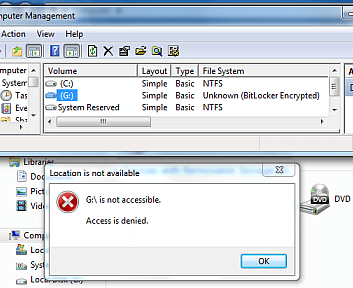
This was my first worry after I turned BitLocker on for my Windows 8 Pro laptop. So I decided to test and see what happened. Playing a hypothetical hacker thief, I took my drive out and connected it to a vanilla Windows 7 bench system we have at our company office. This was to simulate what a low-level criminal would likely do to try and see what data I had on my drive. The below image shows that my BitLocker protected drive, in this case Drive G, was fully inaccessible to a mere drive-by data theft attempt:
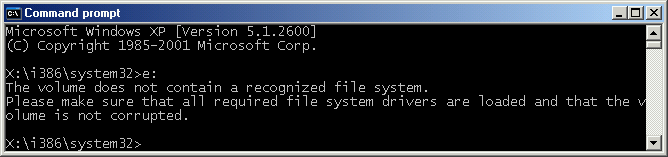
Going a step further, I decided to give Mini Windows XP a try off Hiren’s Boot CD 15.2. This a hidden gem in my toolkit for extracting data from drives that just won’t function properly in a stock Windows installation, even when connected to a third party system. Mini Windows XP simulates a WinPE-based environment that replicates a majority of the core operation of Windows XP but without any of the hassle of traditional installation – the entire instance runs right off the Hiren’s CD like a Linux Live CD.
Upon attempting to access my disk through the command prompt in Mini Windows XP, this is the error I got:
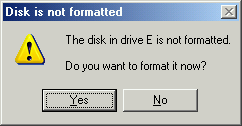
And trying to browse into the drive through the Mini Windows XP explorer got me no further than this:
Am I a full blown computer security expert? Not by any means. But in replicating the procedures that about 95% of thieves would likely try on a stolen laptop, BitLocker surely has the brute entry attempts thwarted to a high degree.
Is BitLocker foolproof? Can it be hacked?
As long as humans are involved, it is said, no technology is ever foolproof. BitLocker is no exception. While the TPM method provides security that is quite impenetrable, if someone trying to access your data gets your Windows (or Microsoft Account, in the case of Windows 8) password, your security detail goes out the door. If your password is simple, you may opt to turn on additional PIN security for BitLocker to avoid this pitfall.
It was reported back in 2008 that one of the few ways to get around BitLocker encryption (aside from the poor man’s password hijacking above) is via a so-called “cold boot attack” that culls encryption keys that are still present in memory after system shutdown. You can see a video of the process online as well. The workaround involves a theoretical attacker either booting a system into a special program to extract the still present keys from DRAM, or simply moving the DRAM chips to another machine for analysis and extraction.
While the scenario above is rock-solid in concept, it’s practicality is questionably. First off, most laptop thieves are criminals of chance – taking systems during instances of opportunity like laptops left at coffee shops and library tables. These average Joe criminals are likely not equipped with the tools and knowhow to get such an attack accomplished in the small amount of time (a few minutes or less) needed to be successful. And secondly, this type of attack presumes the laptop and disk drive are still together and operational in the small window afforded for this crack to work.
In practical terms, I highly doubt the effectiveness of a cold boot attack by anyone but the most seasoned hacker. Even then the process is a crap shoot that plays on chance and luck. If I were putting my computer’s data security in the hands of BitLocker, I’d feel pretty safe even knowing about cold boot attacks. There are no recorded instances I could find online proving that cold boot attacks were prevalent in the face of BitLocker protection.
How simple is BitLocker to setup for full drive encryption?
The process is quite simple, and only entails a few clicks to get up and running. The step by step tutorial provided below simulates the procedure on a stock Windows 8 Pro machine, assuming the end user wants to encrypt their boot (C) drive with BitLocker. The steps are similar, but could vary a tad, for other flavors of Windows. Here are respective guides from Microsoft for using BitLocker on Vista and Windows 7.
For a Windows 8 machine, here is all it takes:
1) Go into the Control Panel and click on BitLocker Drive Encryption. My demo assumes you are viewing the Control Panel in technician-friendly icon view.
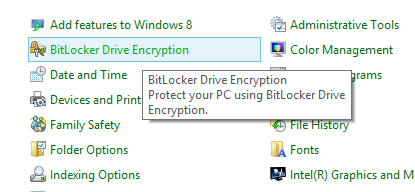
2) Find the drive you want to encrypt and select the “Turn on BitLocker” option beside it. For me, I wanted to encrypt my main boot drive (C) so this was fairly straightforward.
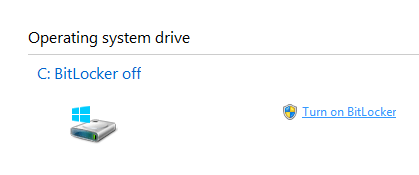
3) You are going to be asked how you want to save a backup of your recovery key. The recovery key allows you a last-resort option to re-enter your drive if you run into a situation where your TPM enabled system is broken, or you otherwise lost access to the drive. For people on a Windows domain, you can back up to AD. Since my laptop is not part of a domain, I was given a choice to save my key to my Microsoft account, save it to a file, or print the recovery key. I decided to merely save it to a file on my office NAS box.
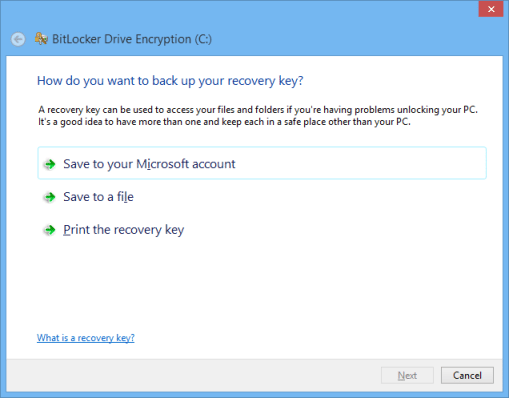
4) You will be asked if you want to encrypt only the space used by data, or if you want to cover the entire drive. My recommendation is to always do the entire drive as I see no sense in just locking down a portion of it. Unless time is not on your side, choose a full drive encryption here.
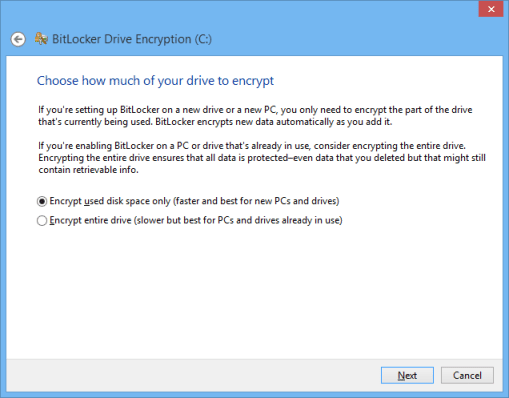
5) A final warning will ask you to do a system check before enabling BitLocker fully, which is highly recommended. This will force Windows to do an integrity check on the keys it has created to ensure you can regain access to the system after BitLocker goes on. I’m sure the system is pretty self-assuring, but it never hurts to force a final check before going all-in with BitLocker.
After your prompted reboot, BitLocker encryption goes to work in getting your drive secured either partially or fully, depending on what you chose in step 4.
6) The encryption process can take some time. My Windows drive is a 256GB OCZ SSD and I decided to encrypt my entire disk (the recommended option) and it took about 3-4 hours to complete if I recall. The best part was that I could fully use my computer while it was working – it’s not like it held my system hostage. You can check encryption status at any time by double clicking on the system tray icon that shows during the process.
7) Once encryption is complete, you should see a window like this:
Going into My Computer now provides you with a similar looking C drive with a shiny, neat lock icon going forward, denoting BitLocker functionality being enabled:
And that’s it! BitLocker is now working and you can rest assured that your data is safe if your hard drive or laptop is lost, or otherwise ends up in the wrong hands. With the introduction of Windows 8.1 later this year, every system running any flavor of Windows 8 will have some form of BitLocker (or drive encryption) capability caked into Windows, so there should be no excuses going forward as to why your customers or your own workers cannot benefit from this feature.
As more and more of us carry around critical, sensitive company and client information in our backpacks and carry-ons, it is becoming ever more important to have a layer of security in place to prevent such data loss. Wishing you had this free and easy technology turned on after hardware loss is not a position you want to place yourself or your clients in.
Do you already employ BitLocker, or a competing technology? What’s your take on full drive encryption for portable devices? Let us know in the comments area below!
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

I’m all for encryption as long as there’s an unencrypted backup of the data.
I very often do simple data recovery from logically dead (meaning the hw is fine) drives.
On encrypted drives there nothing to do, other than cry over spilled milk.
Make sure that your client knows how to do backups, does backups and tests those backups. Because if his drive gets scrambled there goes the info.
I use Cobian which is basically a simple file copy so its easy for a user to check that it’s working.
We have been using BitLocker for a couple years now along with 802.1x for our wireless connectivity. Field clients are our biggest problems with BitLocker is with hard drive problems. If a drive has a bad sector or is becoming corrupt the BitLocker will activate and lock the drive down. Lastly, we also ship to all clients with their quarterly lease refresh a Lacie BackUp Drive with the software for unencrypted backups of their entire profile and any additional files that they may store on the root of the drive. Many of our laptops have been stolen while clients are traveling or stolen from their vehicles, why they left there laptop in there car overnight is beyond me, the BitLocker provides assurance that their data is unreadable.
I’ll second the caution that backups are especially important if you plan on using full drive encryption. That is one reason I am very cautious about who I set it up for. That, and I have plenty of clients that would forget their password and get locked out that way.
Agree with everyone’s thoughts. We use TrueCrypt, but the worry is always the drive will die or have bad sectors and recovering from an encrypted drive like this can be very difficult (and super expensive if level-3 data recovery is needed).
My guess is more people loose data to hard drive problems than theft. So it’s safer to stay unencrypted with a decent chance for recovery when your drive dies.
In the future, for our backups of client data, maybe we’ll try BitLocker since it sounds much more seamless. Thanks for the info!
If you are concerned about clients losing their password or recovery key, you can always have the key backed up to their Microsoft account or you can offer to keep a copy of the key in safekeeping on their behalf in your own internal storage system or similar:
http://windows.microsoft.com/en-us/windows-8/bitlocker-recovery-keys-faq
Very easy to do and solves the “what if they get locked out” problem. Hope this helps everyone! BitLocker is very neat once you get the hang of it.
I understand the need for data backup, but why unencrypted? The main reason users should encrypt their sensitive data is so NO ONE else can view it. Unencrypted backups allow anyone with access to that backup drive (local or remote) to view the data. I would have an alternate form of encryption for the backup and not just leave the data naked. I have setup TrueCrypt, BoxCryptor and AxCrypt (to name a few) for clients to secure their backups. If the main drive fails with Bitlocker or TrueCrypt you still have the backup that is encrypted with another method. One issue people may find with this is the fact that if there is a fire or flood both encrypted copies of the data would be lost (same as if they were not encrypted). Proactive thinking would bring you to encrypted offsite backups. Whether it would be cloud or backup tape rotation you store offsite these can always be encrypted as well.