Penetration Testing and Security Analysis Tools
Penetration testing is a fascinating subject. Learning how to ethically hack a system in order to find vulnerabilities and prevent malicious hackers from taking advantage of an exploit is a dream for those who love to make money hacking but prefer not to wear orange jumpsuits in an 8’x10’ cell. Let’s take a look at some of the tools of the trade for the penetration tester, most of which are freely available for you to tinker with.
PLEASE NOTE: There are laws restricting port scanning in many areas, even if it’s not malicious. Know that if you you use these tools on a system that you do not have permission to be on you will be subject to penalties.
1. Metasploit
Metasploit is a free open-source security vulnerability scanner. In the Metasploit framework you can actually develop and execute exploit code against a machine or network.
The basic steps for exploiting a system using Metasploit (from Source)
- 1. Choosing and configuring an exploit (code that enters a target system by taking advantage of one of its bugs; about 300 different exploits for Windows, Unix/Linux and Mac OS X systems are included).
- 2. Checking whether the intended target system is susceptible to the chosen exploit (optional).
- 3. Choosing and configuring a payload (code that will be executed on the target system upon successful entry, for instance a remote shell or a VNC server).
- 4. Choosing the encoding technique to encode the payload so that the intrusion-prevention system (IPS) will not catch the encoded payload.
- 5. Executing the exploit.
The two most common payloads generated from Metasploit are:
1. Command shell that enables users to run scripts and commands against the host.
2. Meterpreter enables users to control the screen of a host machine using VNC.
Metasploit can also import vulnerability scan data and compare the identified vulnerabilities to existing exploit modules for accurate exploitation.
Armitage is a graphical interface front-end to the Metasploit framework that makes it easier to carry out security attacks.
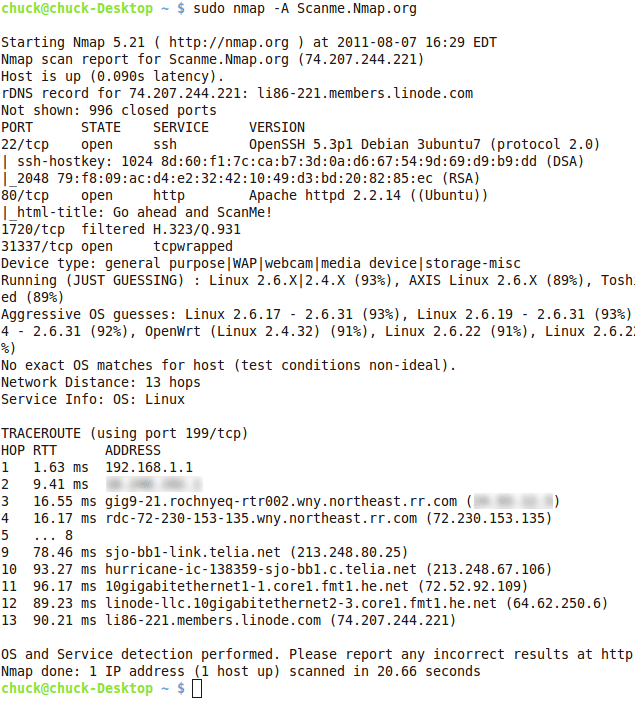
2. NMap (Network Mapper)
NMap is another great penetration testing tool. It is an open-source network scanner (port scanner) that finds host, services, and port information. You can use NMap to scan a network for open and insecure ports, host systems, and servers. It can also be used for simple network inventory and maintenance by detecting operating systems, versions, and even hardware information. It’s fairly simple to use, yet very powerful in the hands of an experienced technician/hacker.
3. Nessus
Nessus is a proprietary vulnerability scanner. They offer a free version for personal and non-commercial use. Commercial and enterprise usage requires a license fee. Nessus can be used for auditing a network, vulnerability discovery, compliance verification, misconfiguration, and more. The software can also launch third party tools to hack passwords (Hydra) and scan ports (NMap).
4. Wireshark
Wireshark is free and open-source packet analyser (commonly known as a packet sniffer). Basically it will report and capture any traffic within a network. Data can be captured and read later or you can watch packets in real-time. Wireshark is a great tool to assess network bog-downs, malicious/suspicious traffic, protocol analysis, and even capturing raw USB traffic (currently available only in Linux).
5. Cain and Abel
Cain and Abel is a password recovery tools (password cracker) for Windows. It uses dictionary attacks, brute-force, and cryptanalysis as well as methods to decode encrypted passwords.
6. John The Ripper
John the Ripper is a password cracker that will run on Linux/UNIX, Mac OSX, and Windows. It is free and open source software.
7. Snort
Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort uses signature, protocol, and anomaly-based inspection methods to detect malicious traffic trying to enter or probe a network. It can also be used as a packet sniffer and a packet logger. Snort will run in a Linux/UNIX and Windows environment.
8. Kismet
Kismet is a powerful packet sniffer, and intrusion detection system for 802.11 wireless LANs.
“Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, decloaking) hidden networks, and inferring the presence of nonbeaconing networks via data traffic.” – http://www.kismetwireless.net/
9. HPing3
HPing3 is a supercharged version of the Ping command utility. HPing3 can use TCP, UDP, ICMP and RAW-IP protocols other that just ICMP (as ping). It also has a built in traceroute mode.
“This tool is particularly useful when trying to traceroute/ping/probe hosts behind a firewall that blocks attempts using the standard utilities.” -http://sectools.org/
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

Is it just me or did the Technibble theme just change? Looks good Bryce
Liam
It has changed. Lots of additional features too such as threaded comments. Ill announce it all soon.
It never hurts to know extra things :)
Good article, hopefully there’s more articles like this in the future.
I bought a Book Called Ethical Hacking once. It came with a lot of utilities, most of which I would never use in computer repair, but it helps to get a deeper understanding of Windows and the Internet so you can be more effective at repairing customer’s infected computers. BTW, I like your Theme, it is very clean. Would you be willing to share the name of your theme?
Its custom. Was designed by a Technibbler actually.
Metasploit on Technibble? I never thought I’d see the day…
Missed the page where you’ve arranged all the Tools in one place. Now I can’t find the tools we used see in the previous theme. Any way we can be given a link so we can get access to those wonderful tools again.
Thanks.
Brought this back. It definitely is the better way than just the list.
Awesome! Good to have the links back.. and it definitely does makes it easier to browse. Many thanks!
Love the new look of Technibble! This is such a good site. Okay, thanks for this article. I wish they would involve pen testing and security analysis at my local college. This will be a big step forward for us looking to get down on some hackery…
I’m so lucky to be living near a college that offers classes on Ethical Hacking, Penetration Testing, and CISSP. I’ve taken a few classes for a couple of years now and will be getting my Academic Certificates in Network Security and Cisco Routing & Switching this Fall.
I’m familiar with all those tools and have used them in class.
Great article Chuck. It was a pleasant surprise to see each of these tools discussed here. I’m proficient with all of these tools except for HPing3, and only know about Kismet . I need to try it out. Thanks again for the read.
its always good to know little more. Thank you for sharing. Security is very important for personal computers and business systems.