thecomputerguy
Well-Known Member
- Reaction score
- 1,467
Client asked me to provide a laptop for an employee to be able to access their SQL Server Database remotely. I am using OpenVPN as the connector.
Connecting to the network is fine, and browsing network resources works fine. User has full access to all resources. The network is configured as a Domain. The laptop is just configured as a standalone device in Workgroup.
I connect through the VPN and browse to the server at \\10.10.0.100 or \\server after which I am prompted for credentials. I manually type the credentials in the for user and store them. This allows me access to all of the network resources.
When attempting to run the program I get this error:
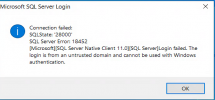
Followed by:
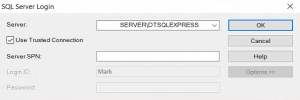
I took the laptop onsite and the issue did not change.
As a testing method I joined the laptop to the Domain after which the connection to the SQL Server worked fine.
It worked fine until I took the laptop offsite again and then it wasn't using the onsite Domain Controller as a DNS server (Probably because it was no longer authenticating).
I found a few articles: (https://techyaz.com/sql-server/trou...452-login-failed-login-from-untrusted-domain/) that mentioned to make sure that the SQL Server was set to 'mixed' mode for authentication in SQL Management Studio.
I logged into SQL Management Studio and 'mixed' mode was already selected.
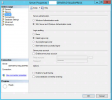
What is the most painless way to make this work? I don't want to get into any heavy lifting on this one. I just want it to work.
I have since returned the laptop to Workgroup as a standalone station.
Admittedly I don't know a whole lot about SQL, and neither does their support department apparently.
Connecting to the network is fine, and browsing network resources works fine. User has full access to all resources. The network is configured as a Domain. The laptop is just configured as a standalone device in Workgroup.
I connect through the VPN and browse to the server at \\10.10.0.100 or \\server after which I am prompted for credentials. I manually type the credentials in the for user and store them. This allows me access to all of the network resources.
When attempting to run the program I get this error:

Followed by:

I took the laptop onsite and the issue did not change.
As a testing method I joined the laptop to the Domain after which the connection to the SQL Server worked fine.
It worked fine until I took the laptop offsite again and then it wasn't using the onsite Domain Controller as a DNS server (Probably because it was no longer authenticating).
I found a few articles: (https://techyaz.com/sql-server/trou...452-login-failed-login-from-untrusted-domain/) that mentioned to make sure that the SQL Server was set to 'mixed' mode for authentication in SQL Management Studio.
I logged into SQL Management Studio and 'mixed' mode was already selected.

What is the most painless way to make this work? I don't want to get into any heavy lifting on this one. I just want it to work.
I have since returned the laptop to Workgroup as a standalone station.
Admittedly I don't know a whole lot about SQL, and neither does their support department apparently.
Last edited:
