thecomputerguy
Well-Known Member
- Reaction score
- 1,407
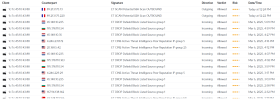
Client has a camera system which is accessible via a mobile app as well as a web browser. Ports are required to be opened to make this work... specifically (Vitek Cameras).
TCP/UDP 5000
TCP/UDP 443
TCP/UDP 8000
TCP/UDP 631
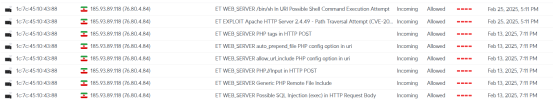
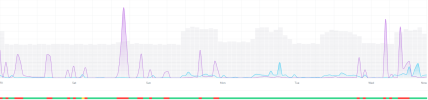
Client was complaining that their internet was intermittently dropping. I started troubleshooting and when sifting to logs I was seeing that their DVR was getting pummeled due to the open ports. Every time their internet cut out the DVR uploaded a massive amount of data which shut them down. See the graph below:
All purple spikes are the DVR sending data and then the internet drops hence the red outage.
What is the correct way to do this these days. I know this is an old school setup and open ports = BAD.
I've since disabled the port forwarding.
Is this a VPN in and then accessing the cameras that way type of situation?
TCP/UDP 5000
TCP/UDP 443
TCP/UDP 8000
TCP/UDP 631
Client was complaining that their internet was intermittently dropping. I started troubleshooting and when sifting to logs I was seeing that their DVR was getting pummeled due to the open ports. Every time their internet cut out the DVR uploaded a massive amount of data which shut them down. See the graph below:
All purple spikes are the DVR sending data and then the internet drops hence the red outage.

What is the correct way to do this these days. I know this is an old school setup and open ports = BAD.
I've since disabled the port forwarding.
Is this a VPN in and then accessing the cameras that way type of situation?
Last edited: