thecomputerguy
Well-Known Member
- Reaction score
- 1,453
I will start off by saying I'm a noob when it comes to Intune or Azure AD. I have had this issue across all of my tenants not just this new one and I just haven't had the time to figure it out and research why this is happening. When I sign into a Business Premium account on a computer across any one of my tenants I get the standard popup.
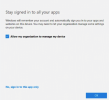
If I leave the checkbox checked in I get this error:
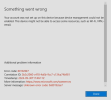
The app will login and function but it will not register the device with the organization at https://intune.microsoft.com/
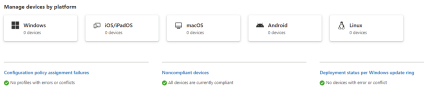
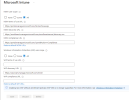
So my tenant show this.
What settings do I need to change to allow the device to register? Here are a couple of screenshots from what I've looked at so far
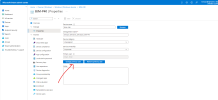
Devices > Enrollment > Automatic Enrollment
-----------------------------
I mainly want the device to register correctly with the organization so I can manage it in Intune then store BitLocker keys there ... Does anyone have the absolute basics I need to do that?

If I leave the checkbox checked in I get this error:

The app will login and function but it will not register the device with the organization at https://intune.microsoft.com/
So my tenant show this.

What settings do I need to change to allow the device to register? Here are a couple of screenshots from what I've looked at so far
Devices > Enrollment > Automatic Enrollment

-----------------------------
I mainly want the device to register correctly with the organization so I can manage it in Intune then store BitLocker keys there ... Does anyone have the absolute basics I need to do that?