carmen617
Well-Known Member
- Reaction score
- 762
- Location
- Boston, MA
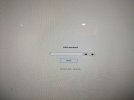
Client let the scammers on his system, and they left him locked up. Haven't seen this particular lock screen before, and doesn't show up in a reverse Google image search. Does anybody recognize it and have a suggestion how to get past it? His data is fine - can access with Hirens and have it backed up, but he is an older handicapped gentleman and I would prefer to at least get to his desktop and see how things are set up before I N&P. The first picture is what you see when you start up system, second is what you see if you hit ctrl-alt-del. There are no restore points on his system, and no reg backup files.