thecomputerguy
Well-Known Member
- Reaction score
- 1,463
I'm so confused. This seems like such a basic function that should be available.
Believe me, CA gives you sooo much more than the "manual way" of doing the MFA under the old 365 admin portal, users section.
With CA, you have such GRANULAR CONTROL of the MFA. You can really customize policies, combinations of certain types, eliminate other types. Multiple Auth method policies and apply to different users groups or to different user devices. Better yet, deny access unless the device is registered or AzureAD joined! Think about that one for a minute!
Not to mention, the absolutely WONDERFUL additions of using "trusted locations" to bypass MFA. And Geo Blocking. Oh the list of benefits goes on and on.
...and then...the list of benefits from other aspects of Biz Prem, such as InTune, and AzureAD P1, and Advanced Threat Protection/Defender....oh my...have a seat for a few hours while we go over those benefits. Cuz once you include those, the price of 13 to 23 bucks per is now justified a bunch of times. Ease of management, thus saves the client money, unless you volunteer your time. Ease of a user signing into other computers and their user profile auto configures. Less time you're spend doing manual things...less manual bills. Alerting from risky activity. Being able to point to "conditional access being used" for compliance policies. Many insurance agencies want proof of security being implemented. The huge advantages of the additional Defender policies..safe attachments, safe links, much better anti phishing and anti spam measures.

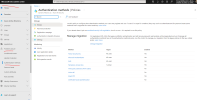
You have this...
View attachment 14521
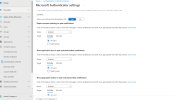
And then can play with specific, such as click into Microsoft Authenticator....enable,apply to all, click into "Configure"....and enable all those 4 settings...
View attachment 14522
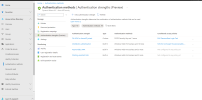
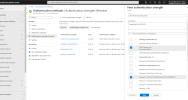
And then you can go into Authentication Strengths....and...oh wow...go to town here....create your own recipies from the list of ingredients...
View attachment 14523
View attachment 14524
Also go into CA policies...and look at the policy templates available to you...
View attachment 14525
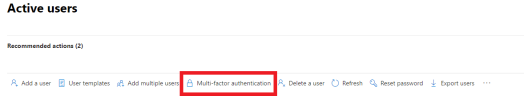
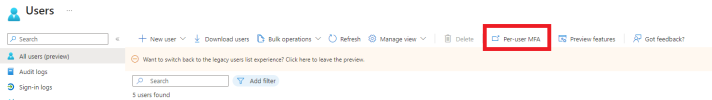
It's not a step backwards, your testing is faulty.
The fact is Security Defaults requires MFA for every login from an "untrusted device".
That means a device that's not associated with the tenant.
So if you logged in from a machine that has a TPM module in good working order the security ID of the machine is passed via the auth process. This ID if associated with another successful login can at times allow you to bypass the MFA requirement. However, if you attempt to muck with the security settings of the account, change password, enroll an authenticator etc, those events will always trigger an MFA check.
Stoncate is right though, if you want full control to say ALL LOGINS MUST, you have to have Conditional Access. I'm not willing to say that Security Defaults isn't secure. However I can fully understand why it would get people's hackles up.
Also, there's a further wrinkle... the auth migration process itself plays with all of this and I've seen it take a couple of days to settle down.
The fact is Security Defaults requires MFA for every login from an "untrusted device".

We tend to think that administrator accounts are the only accounts that need extra layers of authentication. Administrators have broad access to sensitive information and can make changes to subscription-wide settings. But attackers frequently target end users.
After these attackers gain access, they can request access to privileged information for the original account holder. They can even download the entire directory to do a phishing attack on your whole organization.
One common method to improve protection for all users is to require a stronger form of account verification, such as multifactor authentication, for everyone. After users complete registration, they'll be prompted for another authentication whenever necessary. Azure AD decides when a user will be prompted for multifactor authentication, based on factors such as location, device, role and task. This functionality protects all applications registered with Azure AD including SaaS applications.
Ok if they aren't getting rid of it then I'm done for the day. I totally understand the benefits of all this azure stuff but a lot of my clients are in their 60's and are only still working because they don't want to be stuck at home with their spouses or they can't stop working because we're in California and you have to make $250k a year on two incomes just to survive with a family.
My older clients are all on MSP and pay REALLY well. My younger clients just wing it themselves as best as they can and call me when needed.
My plan as a one man MSP is to make this work as well as I can until I'm around 45 which is right around where I'll probably start losing some of those clients due to age... make enough money to float my family for awhile and get out of this. I'm 38 and I've already been doing this for 21 years! To say I'm burned out is an understatement.
All of that was really off topic but I'm trying to paint the picture. I just recently got into the MSP gravy train and I'm gunna ride it as long as I can without complicating mine, or my clients lives.
Slightly off topic: Just curious what your work plan is after 45? Or maybe you've earned enough to retire? Probably unlikely in California lol. I'm just curious. I'm around your age and I see the same thing you mentioned with clients. I think I have at best another 5-10 years of good decent work and then it's going to taper off because a lot of these folks will either be retired or unfortunately no longer amongst us.
I don't get a ton of work from people my age range. Certainly not enough to make a living from that's for sure. A lot of my business clients are in their 60's now like you mentioned. I believe most will retire by 70 or before. Maybe I'll be wrong and things will still be going strong but I'd definitely need to pickup a lot of new clients in the next decade to keep rolling. I have no idea what other kind of work I'd even want to do at this time.
And to not have one, sounds terrifying ... and exciting.
MFA Migration Process
Enable Security Defaults
Azure AD > Overview > Properties > Enable Security Defaults
Make note of Legacy MFA options
Buy Azure Active Directory Premium P1 OR Business Premium and assign the license to backdoor Admin.
- Admin Center > Users > Multi-Factor Authentication > Service Settings
- Make note of all Service Settings
Match Legacy MFA Options in Azure
Begin Migration
- Azure AD > Authentication Methods > Match Legacy MFA options.
- Microsoft Authenticator
- SMS
- OATH
- Microsoft Authenticator Settings > Configure > Allow use of Microsoft Auth OTP
NOTE: This allows Legacy MFA options to Migrate to Azure AD Authentication Methods
- Azure AD > Authentication Methods > Policies > Manage Migration
- Migration In Progress
Disable Legacy MFA options
Disable Password reset options
- Admin Center > Users > Multi-Factor Authentication
- Disable All Accounts
- Service Settings
- Disable all Service Settings
- Disable Allow app passwords to sign in
Azure AD > Protect & Secure > Password Reset > Disable all options
Complete Migration
Azure AD > Protect & Secure > Authentication Methods > Manage Migration > Migration Complete
NOTE: Legacy MFA options are now unavailable
Enable Basic Conditional Access Policies
OPTIONAL: Check authentication methods for users
- Azure AD > Overview > Properties > Disable security Defaults
- Azure AD > Protect & Secure > Conditional Access
- Require multifactor authentication for admin
- Block legacy authentication
- Require multifactor authentication for all users
OPTIONAL: Revoke Authentication methods
- Azure AD > Users > Select user > Verify Authentication methods
- Delete if Necessary
Azure AD > Users > Select user > Authentication methods
OPTIONAL: Require re-register multifactor authentication
Azure AD > Users > Select user > Require re-register multifactor authentication
OPTIONAL: Password resets
BEGIN THE ONSLAUGHT
Other Conditional Policies (ALL):
Clean up Microsoft defender
- Require multifactor authentication for admins
- Require multifactor authentication for all users
- Block legacy authentication
- Require MFA for admins
- Require MFA for external and guest users
- Block all legacy sign-ins that don’t support MFA
- Require MFA for internal users (admins not included) – Basic
NOTE: Safelinks, Anti-spam, Anti-phishing, Safe attachments, Safe links
- Admin center > Security > Improve your score
- Address Scoring issues
Default policies enabled by default
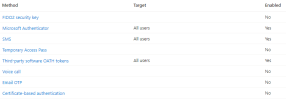
- Require multifactor authentication for admins
- Require multifactor authentication for all users
- Block legacy authentication
- Require MFA for admins
- Require MFA for external and guest users
- Block all legacy sign-ins that don’t support MFA
- Require MFA for internal users (admins not included) – Basic
1 - Users can setup Mobile#/SMS under their account when they are logged in or you can do it in Azure for them. We do it in Azure to take the work off of the end user.I wrote out this MFA migration process maybe someone can take a look at it:
I still have a couple of questions
1.) Add SMS as an option of MFA in Azure. Even though it is listed as an option in Azure it is not an option when a user first logs on. The only option is to use the Microsoft Authenticator with PUSH for ALLOW when login is attempted. I see this as a problem since people will inevitably click allow when they shouldn't.
View attachment 14531
2.) Is there an option to require a OTP as opposed to PUSH and ALLOW via the Microsoft authenticator WITHOUT the user having to click "Use a different authenticator app"
This will not happen, users are dumb
I see this as a problem since people will inevitably click allow when they shouldn't.
3.) Is there an option to revoke all authenticators from a user?
4.) What are the best practice, basic conditional policies that would protect the tenant from bad logins, currently I have:
Some of these are redundant as I had defender automatically create some of them when I was addressing the security score.
5.) I typically insert myself as a backdoor admin for the tenant. In the past I would create my account, add myself as global admin then enable Legacy Multi-Factor authentication
Does this mean that my backdoor admin account now requires an Azure AD Premiem P1 license OR Business Premium License to match the tenant?
I know I can probably get around this by using the MS Partner portal which I have an account for but do not currently use. I typically login to the tenant I am managing per my backdoor tenant login.
 But honestly if you're not familiar with CA policies and you need to get some form of MFA enforced for all users, just enable secdefs. That's the quickest way to do it. You can always come back and work on CA after you learn more about it.
But honestly if you're not familiar with CA policies and you need to get some form of MFA enforced for all users, just enable secdefs. That's the quickest way to do it. You can always come back and work on CA after you learn more about it.1 - Users can setup Mobile#/SMS under their account when they are logged in or you can do it in Azure for them. We do it in Azure to take the work off of the end user.
2 - You can enable number matching with MS Authenticator app
3 - I know there is some powershell commands based on old MSOL module to reset a users MFA but I havent used it in a while so I do not recall if it deletes their registered mfa devices or not.
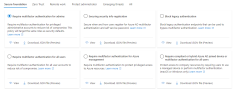
4 - See the template policies in Azure portal:
View attachment 14533But honestly if you're not familiar with CA policies and you need to get some form of MFA enforced for all users, just enable secdefs. That's the quickest way to do it. You can always come back and work on CA after you learn more about it.
5 - we've never licensed admin or management accounts. I dont think it's required but I dont have any official reference on that.
Require users to do multifactor authentication when necessary
We tend to think that administrator accounts are the only accounts that need extra layers of authentication. Administrators have broad access to sensitive information and can make changes to subscription-wide settings. But attackers frequently target end users.
After these attackers gain access, they can request access to privileged information for the original account holder. They can even download the entire directory to do a phishing attack on your whole organization.
One common method to improve protection for all users is to require a stronger form of account verification, such as multifactor authentication, for everyone. After users complete registration, they'll be prompted for another authentication whenever necessary. Azure AD decides when a user will be prompted for multifactor authentication, based on factors such as location, device, role and task. This functionality protects all applications registered with Azure AD including SaaS applications.
