This is very interesting to me and may be what I am looking for. Although I have heard of the term "overlay network", I never knew what it really entailed. Based on a little bit of research, are you referring to say...running the DC server on a VM and creating virtual switches? As I said before, I would never run a server open to the internet but was just curious as to if it could be done when setting up a domain and DCs.
Toss ZeroTier on the DCs and they're now on the same LAN as each other regardless of where they go. Connectivity issues are resolved with a ZeroTier One service restart via the RMM tool, which can be automated and tested.
I do not share Stonecat's concerns about hardware being magically more reliable, and I've seen VASTLY improved performance with ZeroTier since it's based on Wireguard VPN technology, which is several orders of magnitude better than IPSec, and at least one order of magnitude better than OpenVPN.
And if you want to Zero Trust it, apply a policy to ZT that only allows the two servers to communicate with specific protocols and ports. That is a bit more hard mode, but it works well once you get your head around the rule structure. Tailscale is "better" on this front, but it's also much more expensive.
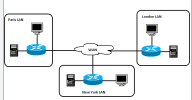
@nlinecomputers That's the new buzz word around what I jokingly refer to as super VPNs. There's a cloud match maker out there that the clients connect to, and there's an authorization process for them to get into the network. But once the magic is all done, each machine gets a NIC on itself that allows it to communicate with the rest of the overlay network as if it's just another local LAN. I use ZeroTier myself, and it means that I can put servers and workstations on the same "LAN" even if they're on the other side of the planet from each other. I can define how they can communicate too, so firewall rules basically.
You need to play with them... because once you do I promise even with the ease of Arista Edge NGFW's OpenVPN module, you'll never use it again. IPSec? SCREW THAT!
@YeOldeStonecat If you REALLY want a hardware devices to do the routing, that's what an rPI is for, tutorials are everywhere.