britechguy
Well-Known Member
- Reaction score
- 5,075
- Location
- Staunton, VA
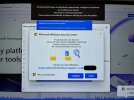
A new client just got scammed yesterday, and this is one of the more convincing versions of this scam I've seen. I'm impressed that she took the photo, but a bit confused as to why she did if she did not have instant suspicion. But she terminated the interaction too late. They'd already remoted in with Teamviewer and asked her to pay them, in Bitcoin, after having removed ESET and noodling around for a while (looking for what, I don't know). She did not pay, and terminated things, but too late.
A completely clean reinstall of Windows was done, and I Fabs-ed her user data off the old and back on to the freshly reinstalled again. I figure if anything was implanted in a user data file either Windows Defender or ESET will detect it.
