Mike McCall
Well-Known Member
- Reaction score
- 1,073
- Location
- Silverton, Oregon
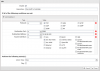
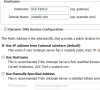
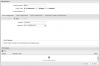
This is one of the problems when trying to learn from searches and reading. I've been reading of the importance of segmenting networks for reasons including security. My reasons include separating bench work access from the main LAN, VOIP, and media streaming. Minimizing the additional traffic is a side benefit, though the network is small enough for that to really be a non-issue.
Though I'm reluctant to claim I know my own name at times, I do know the difference between a VLAN and an IP Network. While I had to memorize the OSI model, there was no context for it or instruction on how to use it in a practical sense. I've tried to make use of a lab to learn some things, but it's weakness is not having anyone to check my work and show me what I missed or got wrong. Many techs get to work for someone else who can help teach them, while others get to "grow-up" on their own. The latter is a longer process. Like many others here I didn't get to have someone mentor me. Not complaining, just noting. I take what I do seriously and want to do it well. More than anything else, that's what I want others to see in me.
Though I'm reluctant to claim I know my own name at times, I do know the difference between a VLAN and an IP Network. While I had to memorize the OSI model, there was no context for it or instruction on how to use it in a practical sense. I've tried to make use of a lab to learn some things, but it's weakness is not having anyone to check my work and show me what I missed or got wrong. Many techs get to work for someone else who can help teach them, while others get to "grow-up" on their own. The latter is a longer process. Like many others here I didn't get to have someone mentor me. Not complaining, just noting. I take what I do seriously and want to do it well. More than anything else, that's what I want others to see in me.